If you remove authentication from a request and your API still can’t answer with a clean 401 Unauthorized, you don’t have a “small backend detail”. You have a system that lies to its clients. And once an API starts lying, every bug hunt becomes slower, noisier, and more expensive.
This is one of those checks people dismiss as “obvious” — right until they spend 45 minutes debugging a request payload that was never the problem.
What was tested
Rentgen takes a request that includes authentication (cookie or bearer token), then removes it entirely and sends the same request again. The expectation is simple: when the client is not authenticated, the API must say it clearly.
What Rentgen found
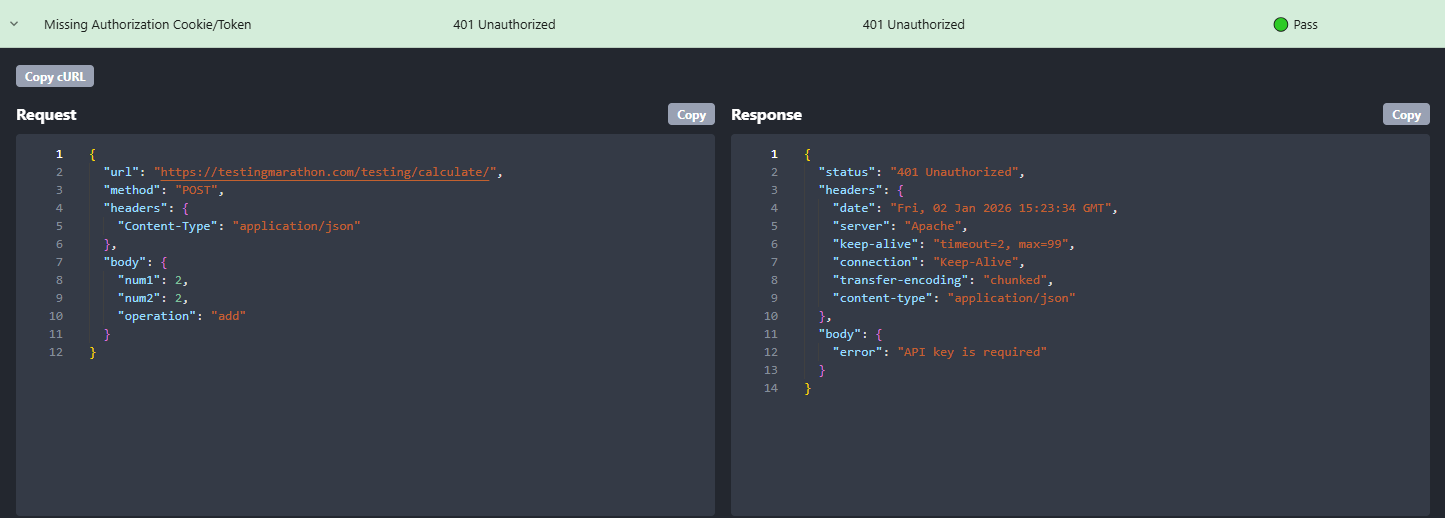
- TEST: Missing Authorization Cookie/Token
- Expected:
401 Unauthorized - Actual:
401 Unauthorized - Status: 🟢 Pass
Why this test exists
Because most teams don’t break APIs on purpose — they break them accidentally.
Someone forgets to pass a cookie.
Someone drops an Authorization header during refactoring.
A mobile WebView behaves differently.
A gateway strips headers.
A proxy behaves like a “helpful” middleman.
In those moments, the API response is not just a status code. It’s a navigation sign for developers. A good sign gets you home fast. A bad sign sends you into the desert.
401 vs 403 — not semantics, pure debugging physics
Here’s the hard rule:
- 401 Unauthorized means: “I don’t know who you are.” → authentication problem
- 403 Forbidden means: “I know who you are, but you’re not allowed.” → authorization/permissions problem
When an API returns 403 for a request that has no authentication at all, it’s giving the client a fake story. The client hears: “You are logged in, but you don’t have access.” So people start checking roles, scopes, feature flags, policies, user groups… while the real issue is brutally simple: there is no token.
That’s how a one-second fix becomes a 30–60 minute debugging session with three people and a Slack thread.
Why 400 is also wrong
If you send a request without authorization and you get 400 Bad Request, the API is basically saying: “Your payload is invalid.” Developers then start polishing JSON, validating types, comparing request bodies — and the API quietly hides the real reason it rejected the request.
Authentication must be handled before business validation. Otherwise your API becomes one big “guess what I meant” machine.
And yes, 500 is the loudest red flag
I’ve seen APIs return 500 Internal Server Error when authorization is missing. That’s not “edge case”. That’s an architecture problem: unhandled nulls, broken middleware chains, or authorization logic tangled with runtime assumptions.
Even if nobody “hacks” anything, it signals something ugly: your API can be crashed by ordinary client mistakes.
What the market does in practice
In case studies, this check is surprisingly often broken — including in big, mature products. The most common failure is returning 403 for missing auth. Teams build permission layers, gateways, policies… and still forget the first, boring contract: no auth = 401.
Why does it happen? Because frameworks sometimes “help” by defaulting to 403. Because middleware is copy-pasted. Because “it works for us” becomes the only requirement. And because nobody likes writing tests that feel too obvious to be tested.
How to fix it
The pragmatic rule:
- If there is no authentication (missing/empty/absent token) → return
401 - If authentication is present but user lacks permissions → return
403 - If auth is missing, do not validate business payload first
If you use cookies, make sure the auth layer triggers on missing cookie. If you use bearer tokens, ensure missing header doesn’t fall into “forbidden by default”. For APIs behind gateways, confirm headers are not stripped or renamed. And if you rely on framework defaults, stop trusting them blindly. Defaults are optimized for “works”, not for “debuggable”.
When can you ignore it?
Almost never for protected endpoints. For public endpoints that allow anonymous access, obviously you shouldn’t force 401. But once an endpoint is protected, the missing-auth path must be clean and predictable — because it’s the most common failure mode in real life.
Why I put this into Rentgen
Because I’m tired of watching teams lose hours to status code lies. Incorrect auth handling doesn’t just “break security”. It breaks trust in the API’s signals. And once trust is gone, every response becomes suspicious.
This check is fast, deterministic, and painfully revealing. If it fails, don’t debate it. Fix it. Your future developers (and your incident channel) will thank you.
Final thoughts
A good API is not only correct — it’s readable under pressure. When authentication is missing, the API should speak plain HTTP: 401 Unauthorized. No drama. No guessing. No fake permission stories. Just a clear signal that saves time.
