OPTIONS is the most boring HTTP method — which is exactly why it’s dangerous to ignore.
It’s not there for business logic. It’s there so clients, proxies, and browsers can ask:
“What are you willing to do here?”
When an API answers that question with 400 Bad Request, it’s not “strict”.
It’s just non-compliant behavior that breaks real-world flows.
What was tested
Rentgen sends an OPTIONS request to the endpoint (no payload, no tricks) and checks for the baseline
behavior expected from REST-style HTTP APIs:
- Status:
200 OKor204 No Content - Header: an
Allowheader listing permitted methods (for example:GET, POST)
This is not about “pretty headers”. It’s about your API speaking HTTP in a way that other systems can understand.
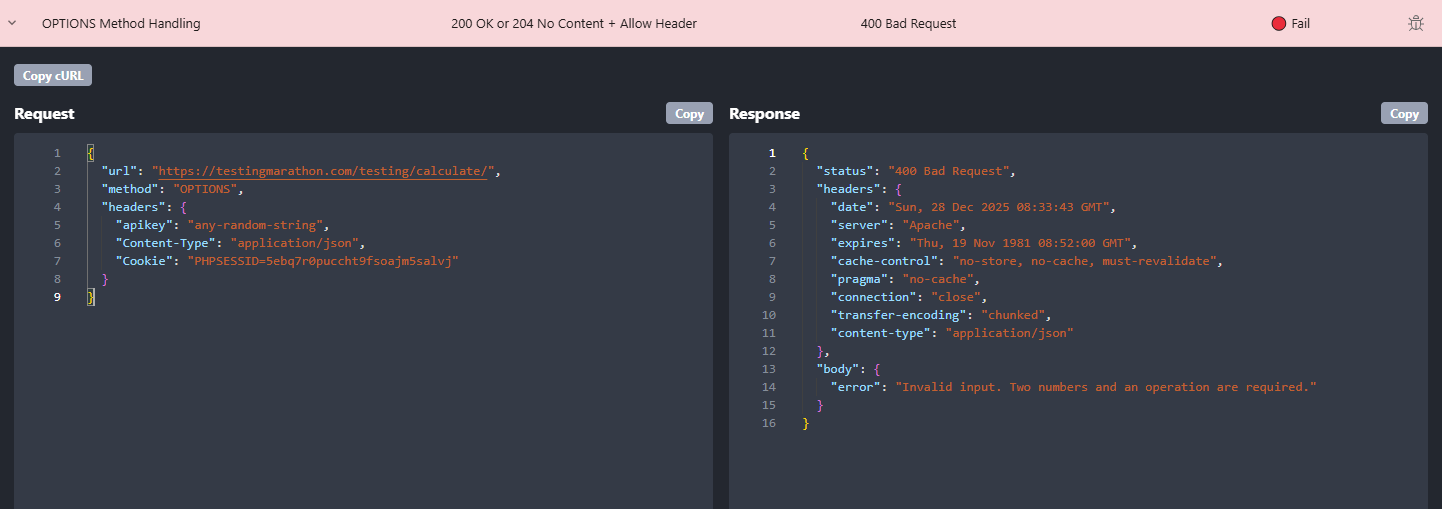
What Rentgen found
- TEST: OPTIONS Method Handling
- Expected:
200 OKor204 No Content+Allowheader - Observed:
400 Bad Request - Result: 🔴 Fail
Why it’s a fail (not a warning)
If you’re building a REST-style API, OPTIONS isn’t optional.
In HTTP terms, it’s a standard way to discover server capabilities.
Returning 400 suggests the server thinks a syntactically valid HTTP request is “invalid”.
That’s a protocol smell.
Rentgen is a REST API testing tool. That means it treats baseline HTTP semantics as requirements. Not because it’s pedantic — but because broken semantics create real operational problems: failing preflights, confusing client behavior, and inconsistent gateway/proxy handling.
What’s the worst that can happen?
Usually it’s not a hacker. It’s a browser.
-
CORS preflight failures — browsers use
OPTIONSbefore cross-origin requests. If it returns400, the real request never happens. - Clients guess incorrectly — SDKs, gateways, and tooling can’t reliably infer which methods are allowed, so they fall back to assumptions or hardcoded behavior.
- Security controls drift — inconsistent method handling often correlates with inconsistent authorization and error behavior (the kind of boring inconsistency that produces incidents).
In other words: you don’t just “fail a test”. You create a system that other systems can’t trust.
Who should take this seriously?
Anyone shipping APIs consumed by browsers, mobile WebViews, front-end apps, third-party clients, or API gateways. If your API is behind a reverse proxy, WAF, or gateway — take it even more seriously, because those layers often make the failure intermittent and harder to debug.
When can you ignore it?
If your API is truly not HTTP-facing (for example, internal RPC over something else) and HTTP semantics are irrelevant.
But if your API speaks HTTP and calls itself REST-ish, ignoring OPTIONS is basically saying:
“We only support HTTP when it’s convenient.”
Why do many APIs still miss it?
Because frameworks make it easy to forget.
A common pattern is middleware or routing rules that only “know” about GET/POST/PUT/DELETE,
and treat everything else as an error — sometimes even before the request reaches the app.
Another pattern: security filters that reject unknown methods early and mistakenly label them as 400
instead of responding with proper method semantics (and proper headers).
How to fix it (the pragmatic default)
The fix is usually not “add a feature”. It’s “stop breaking HTTP”.
-
Ensure
OPTIONSis routed and handled for your endpoints (or at least globally). -
Respond with
204 No Content(often ideal) or200 OK. -
Include
Allowheader listing methods you actually support. -
If this is connected to CORS: make sure the preflight response includes the relevant
Access-Control-Allow-*headers as well.
You don’t need to “implement business logic for OPTIONS”. You need to return the correct capability response — consistently.
Why I put this into Rentgen
Because broken method handling is one of those “small” issues that wastes days in real teams: front-end says “backend is broken”, backend says “frontend is broken”, DevOps says “it’s the gateway”. Then someone finally notices preflight failures and everybody pretends it was obvious.
Rentgen flags this as Fail because it’s a baseline protocol expectation for REST APIs.
If you can’t answer OPTIONS correctly, your API is not behaving like a reliable HTTP citizen.
Copy cURL
Use this to reproduce the finding quickly:
curl -i -X OPTIONS 'https://YOUR-API-ENDPOINT-HERE'What you want to see:
HTTP/1.1 204 No Content
Allow: GET, POST, PUT, DELETEWhat triggered the fail:
HTTP/1.1 400 Bad RequestFinal thoughts
This is not a “security certificate” issue. This is basic protocol behavior. If it passes: great — move on. If it fails: fix it once and remove a whole category of pointless debugging and integration pain.
