(a simple check people forget — until it bites them)
You know that feeling when someone says “security is hard” and you instantly think: no, security is mostly people forgetting obvious things?
This is one of those things.
The Test
No Sensitive Server Headers
Server Header Does Not Expose Version
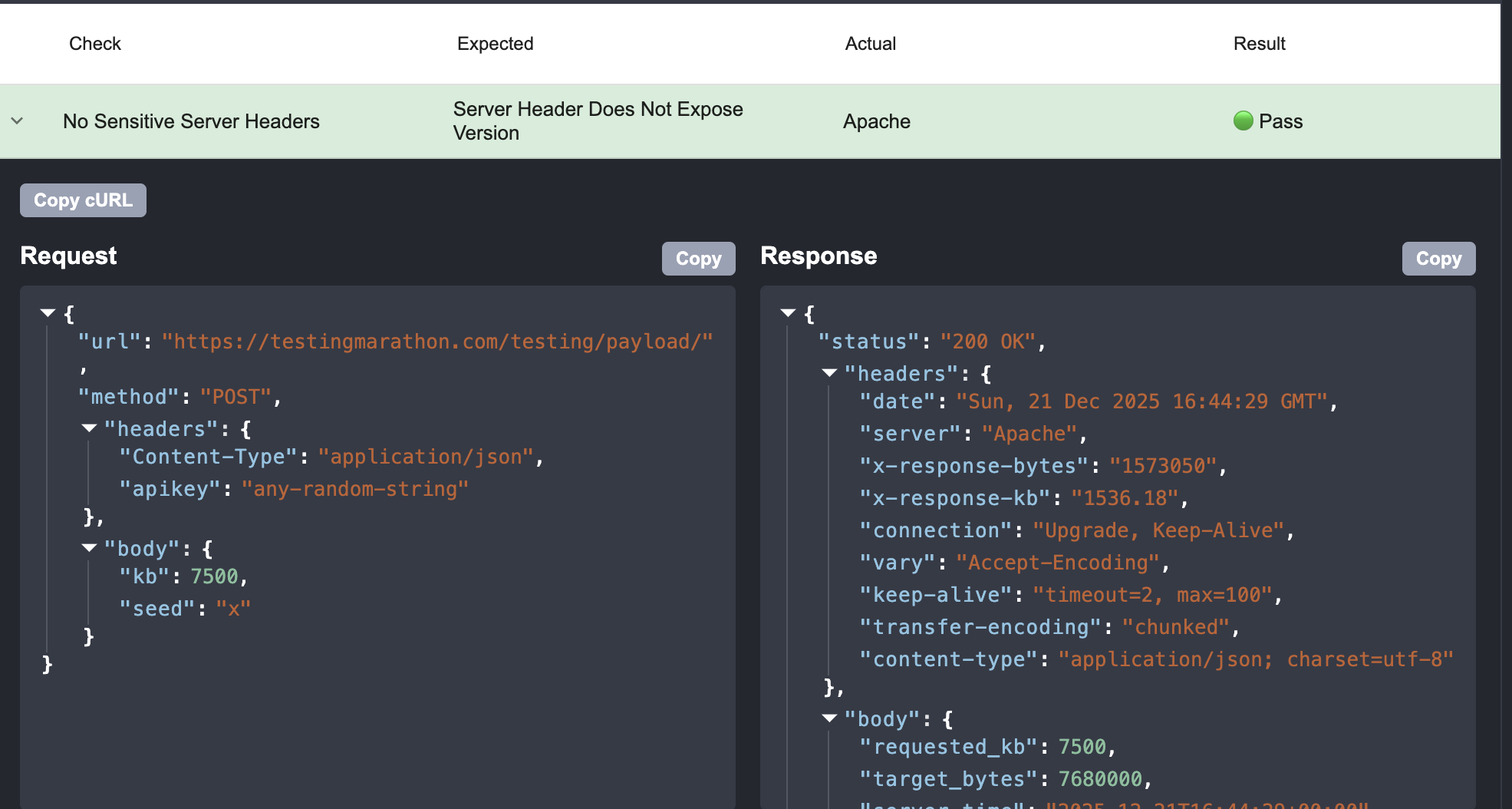
It’s the kind of test that looks almost insulting in its simplicity:
- Call the API.
- Look at the response headers.
-
If you see something like
Server: nginx/1.18.0orApache/2.4.49… you flag it.
No magic. No AI. No “next-gen”. Just reading what the server is casually telling the entire internet about itself.
Why it matters (in real life, not in compliance PowerPoints)
When your server advertises an exact version, you’re basically doing the attacker’s first step for them: fingerprinting.
OWASP calls out that accurately discovering the web server and its version helps
determine whether it’s vulnerable — especially if it’s an older, unpatched version.
OWASP
And yes, attackers do this at scale. They don’t “hack” first. They shop first:
- identify tech
- identify version
- map it to known CVEs
- automate exploitation attempts
“But we patch regularly…”
Cool. Then the test will pass, and everyone moves on.
But here’s why this still matters even for “good teams”:
- You might patch the OS and forget the reverse proxy.
- You might patch nginx but keep an old OpenSSL.
- You might upgrade the app but leave an old gateway container untouched.
- Or you might be perfect… until a rushed hotfix configures “helpful” headers again.
And the biggest problem: this is the exact kind of security check that teams forget because it’s boring. It’s not a failing test suite. It’s not a broken deployment. It’s just a tiny leak… sitting there quietly… waiting.
The “speed of exploitation” problem
Once a vulnerability becomes public, exploitation happens fast — sometimes days fast.
For example, reporting around Apache Struts incidents has described attackers
identifying vulnerable systems very quickly after patches were released.
Krebs on Security
Now combine that speed with version disclosure and you get the ugly reality:
- attackers don’t need to guess your stack
- they don’t need to probe creatively
- they don’t need to “try things”
- they just match what you revealed to what’s exploitable right now
“So what do we do?”
The fix is usually boring too (which is good):
- Configure your server to not disclose the version in headers.
- Keep “banner” details minimal.
- Don’t leak framework or proxy details unless you truly need them.
OWASP explicitly frames this as part of server fingerprinting risk:
older versions without patches are susceptible to known, version-specific exploits —
and learning the version enables targeted attacks.
OWASP
Why I put this into Rentgen
Because people don’t forget hard things.
They forget simple things.
They forget:
- headers
- caching
- redirects
- debug flags
- “temporary” configs that somehow survive for 18 months
So I added the check so this becomes a default habit, not a once-a-year security audit surprise.
It’s the kind of test that won’t make you feel like a superhero.
But it will stop you from being the star of someone else’s incident report.
